Microsoft has exposed Nigerian developer Joshua Ogundipe as the suspected mastermind of RaccoonO365, the world’s fastest-growing phishing operation targeting Microsoft 365 users. The technology giant’s Digital Crimes Unit (DCU) stated it took down 338 websites part of the operation, shutting down the infrastructure used by criminals to steal thousands of user credentials across 94 countries.
RaccoonO365, tracked by Microsoft as Storm-2246, is a phishing subscription service that is very easy for even nontechnical cybercriminals to employ and impersonate Microsoft login pages to collect usernames and passwords.
Since July 2024, the service has been used to steal at least 5,000 Microsoft credentials, with campaigns targeted at industries as sensitive as healthcare. In one case, over 2,300 US organisations were attacked by tax-related phishing emails, and over 20 hospitals and healthcare providers were hit. Microsoft claims the attacks will hold up patient treatment, compromise lab results, and lead to ransomware attacks.
“This case shows that cybercriminals don’t need to be sophisticated to cause widespread harm,” said Microsoft’s DCU in its announcement. “Simple tools like RaccoonO365 make cybercrime accessible to virtually anyone, putting millions of users at risk.”
Unveiling Joshua Ogundipe
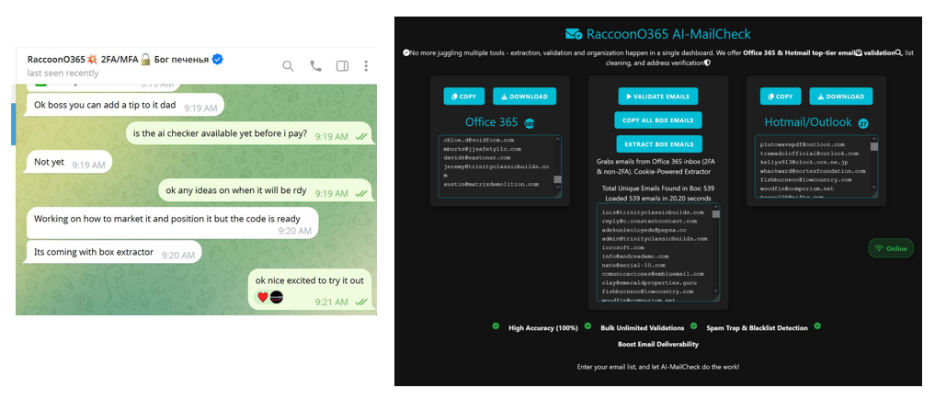
Microsoft’s investigation traced the activity back to Joshua Ogundipe, a Nigeria-based developer who is suspected of having written much of the code that is behind RaccoonO365. Ogundipe and his crew apparently sold phishing subscriptions on Telegram, advertised to over 850 members. They also accepted at least $100,000 in cryptocurrency payments, figures that Microsoft suspects probably fall short of the full reach of the enterprise.
Each subscription gave buyers the ability to send thousands of phishing attacks per day, or hundreds of millions of malicious messages annually. The group also distributed AI-assisted tools like RaccoonO365 AI-MailCheck to allow criminals to bypass filters and boost success rates.
Microsoft says Ogundipe’s gang operated like a startup, coding, marketing their service, and even providing customer support to other cybercriminals. They registered domains with fake names and addresses in a bid to cover their tracks. The most significant breakthrough was made when the group unknowingly compromised a cryptocurrency wallet, allowing investigators to trace their online behaviour back to real identities.

An international criminal referral to world law enforcement has now been made, opening the door for the prosecution of Ogundipe and his crew.
Microsoft’s global coordinated response
The disabling of 338 domains is just part of Microsoft’s strategy to take down phishing infrastructure and serve notice to cybercriminals worldwide. The company worked together with Cloudflare to knock out malicious sites and utilised blockchain analytics software like Chainalysis Reactor in order to trace payments and construct its case.
The tech giant, however, warns that the perpetrators of such activity often seek to recreate their networks following these shutdowns. The company says that it will continue to monitor for new infrastructure related to RaccoonO365 and will take further action legally as necessary.
“This operation shows what’s possible when tech companies, security firms, and governments work together,” Microsoft said. “By disrupting criminal infrastructure, we cut off revenue streams and protect millions of users.”
See also: Microsoft to retire Skype in May 2025, pushes users to Teams
RaccoonO365 demonstrates how cybercrime has become an international, scalable business. Instead of requiring sophisticated hacking skills, prospective crooks can simply buy phishing-as-a-service kits and send mass attacks with the push of a button.
The case further underlines the need for stronger defenses. Microsoft encourages users and companies to enable multi-factor authentication (MFA), keep software current, and train employees to be able to identify phishing attempts, steps that can prevent stolen credentials from blowing up into full-scale breaches.


Microsoft’s action against RaccoonO365 is its most aggressive move yet to fight phishing attacks. For Nigeria, the case emphasises the presence of cyberspace crime networks within its borders and the need for international cooperation to prosecute perpetrators. With Ogundipe named, the fate of RaccoonO365, and the hundreds of millions of phishing emails it enabled, hangs in the balance.








